Last week, we mentioned how a safety crew’s organizational construction can affect a ransomware assault. This week, we dive deeper into how a safety crew’s construction impacts ransomware assault restoration efforts and the way day-to-day cybersecurity outcomes are broadly influenced by organizational construction.
This relies on the Sophos report, “The Impact of Organizational Structure on Cybersecurity Outcomes.”. The firm commissioned a vendor-neutral survey of three,000 IT and cybersecurity professionals from 100 staff and 5,000-person organizations throughout 14 international locations. Part of that analysis evaluated the connection between safety crew construction and safety outcomes, and in that case, which construction produced the most effective outcomes.
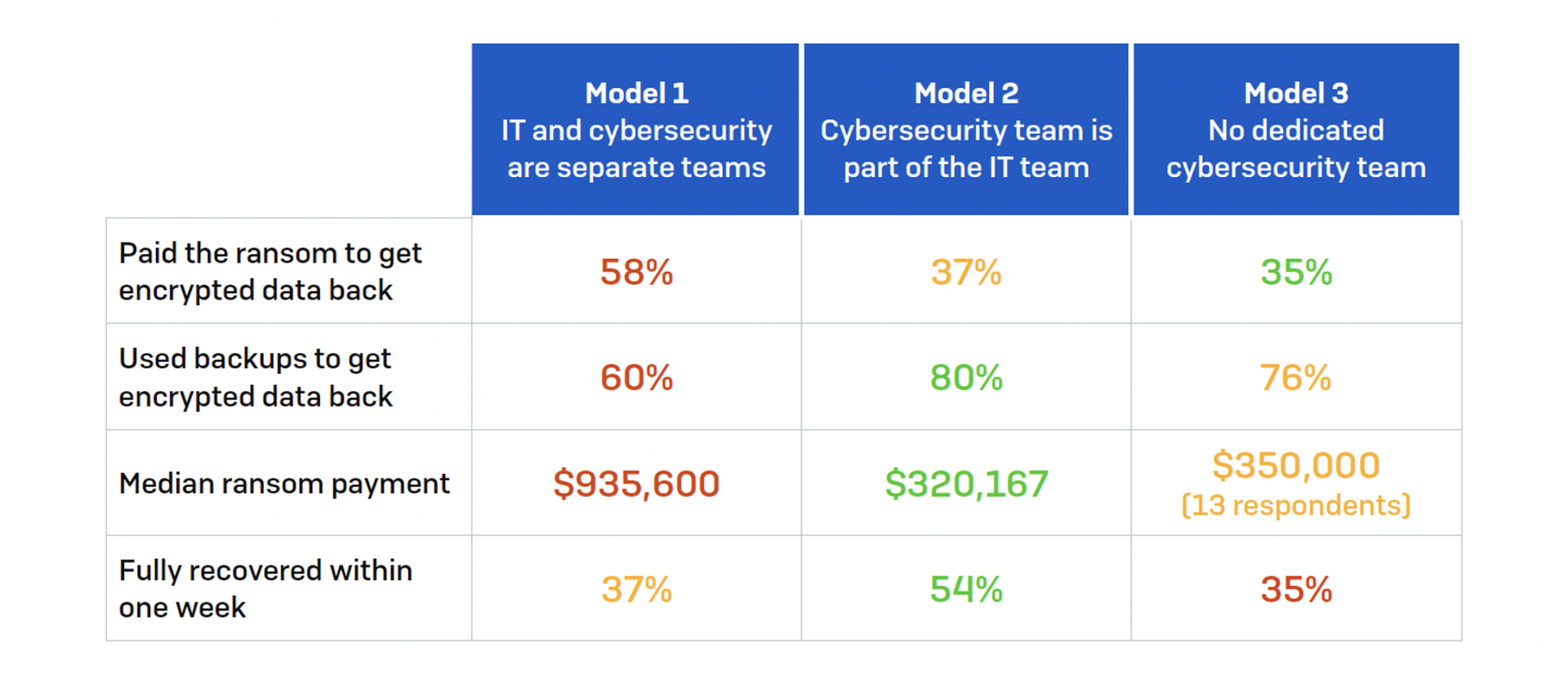
Three fashions evaluated by Sophos:
Model 1: IT and cybersecurity groups are separate organizations (1,212 respondents have been on this class)
Model 2: A devoted cybersecurity crew is a part of the IT group (1,529)
Model 3: There isn’t any devoted cybersecurity crew. Instead, IT groups handle cybersecurity (250)
See final week’s publish for an outline of how organizational construction has affected ransomware affect.
As Sophos factors out, there are two most important methods to recuperate information encrypted by an adversary. You can both use a backup or pay the ransom to get the decryption key. Interestingly, the examine discovered important variations within the propensity and quantity of ransom funds throughout the three fashions.
First, the excellent news is that 80% of organizations inside enterprises the place the cybersecurity crew is a part of the IT crew have been capable of again up and restore encrypted information. That’s the way it ought to be. Organizations with out a devoted cybersecurity crew additionally fared very effectively, with 76% saying they should recuperate from backups. Both teams reported the bottom percentages of survey individuals who paid the ransom, at 37% and 35%.
And due to their low resiliency, it is no shock that Model 1 organizations paid a lot increased ransoms to ransomware gangs. Its median fee was reportedly greater than double that of Models 2 and three. For organizations that adopted Model 1, the median ransom fee was $935,600. At the identical time, Model 2 and three organizations reported common ransoms of $320,167 and $350,000.
The quicker your group can recuperate from a ransomware assault, the higher. More than half (54%) of Model 2 organizations made a full restoration inside 1 week, in contrast with 37% of Model 1 organizations and 35% of Model 3 organizations.
Recovery from a ransomware assault entails many different restoration prices along with the ransom paid. These can embody downtime, excessive insurance coverage premiums, reputational injury, restoration efforts, and extra. In addition to the ransom paid, Model 1 organizations reported that the common ransomware restoration value was $1 million increased than Model 2 organizations: $2.4 million vs. $1.29 million. The Model 3 group was in between the opposite fashions, priced at $1.75 million.
Of course, ransomware prices transcend simply investigating, remediating, and taking backups. It additionally impacts your backside line. Businesses within the Model 1 class have been greater than twice as more likely to report income loss as a consequence of an assault at 57%. This is a major quantity. This is considerably increased than the 31% income loss suffered in Model 2.
Finally, on the subject of day-to-day cybersecurity implications, we discovered that each one three fashions face up to comparable cybersecurity challenges. Still, Model 2 (integrating safety and IT into the identical group) yielded the most effective outcomes amongst all three teams.
Sophos discovered that throughout all three fashions, greater than half report that cyber threats are too superior for his or her group to deal with alone. In mannequin 1 it was 60%, in mannequin 2 it was 51%, and in mannequin 3 it was 54%.
Sophos additionally discovered that there have been comparable considerations throughout the three fashions when it got here to cybersecurity dangers. Data breaches and phishing rank excessive among the many prime three cybersecurity dangers.
Additionally, probably the most generally acknowledged danger total is misconfiguration of safety instruments. “Essentially, everybody has the identical prime considerations, no matter organizational construction,” Sophos discovered.
Another discovering frequent to all three teams: They all moderately wish to spend extra time on strategic initiatives than placing out cybersecurity fires. Although all teams report challenges in these areas, Model 2 organizations seem like higher positioned to take care of day-to-day impacts than these following Models 1 or 3.
This is sensible, as it’s the driving power behind the success of DevOps or “DevSecOps” organizations. Can your group enhance its cybersecurity posture by optimizing IT and safety groups to enhance collaboration? That’s a query value asking.