Secureworks® Counter Threat Unit™ (CTU) researchers are investigating actions by the Iranian Cyber Av3ngers hacktivist group. The group has been linked to assaults courting again to at the very least February 2022. Attacks typically goal Unitronics programmable logic controller (PLC) programs.
While initially investigated as an remoted assault, CTU™ researchers found stories of units from 4 further organizations that appeared to have been compromised on this marketing campaign. Romanian water firm, Factory in Czech Republicsystem for controlling mineral water Czech Republic ingesting fountains,and Pittsburgh Brewery Control System. Devices from different organizations might have additionally been compromised, however haven’t been made public.
In February 2022, Unitronics units related to E-Post parcel distribution facilities in two Israeli cities have been compromised, permitting attackers to remotely open some mailboxes and forestall entry to others. It is now potential. In April 2023, his 10 water managers related to the irrigation programs of a number of farms within the northern area of Israel have been attacked by a cyberattack. In each of those assaults, the message displayed on Unitronics units was just like the message within the Aliquippa assault (see Figure 2). These photographs don’t reference Cyber Av3ngers, however use the identical model and imagery. Messages and targets on Unitronics units counsel that the identical group is accountable for these three assaults. However, the lack of expertise relating to the ways, methods, and procedures (TTPs) and instruments used within the assault makes figuring out the ultimate trigger tougher.
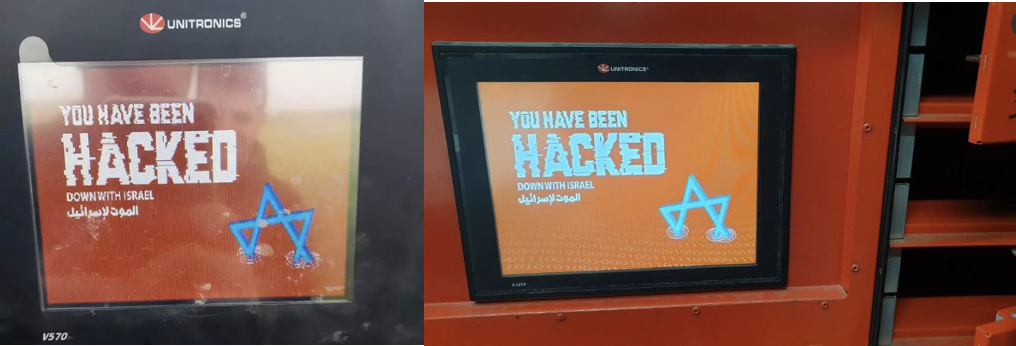
Figure 2. Unitronics show in irrigation facility (left, supply: https://www.jns.org/cyber Attack-shutters-galilee-farm-water-controllers/) and E-Post (proper, supply: https: //firedome) .io/weblog/unitronics-plc-cyber-attack/) Attack.
Unitronics gear is Israeli-made, making it a goal for pro-Palestinian hacktivists. In October 2023, one other pro-Palestinian hacking group referred to as GhostSec claimed assaults on a number of Unitronics units that management water pumps throughout Israel (see Figure 3).
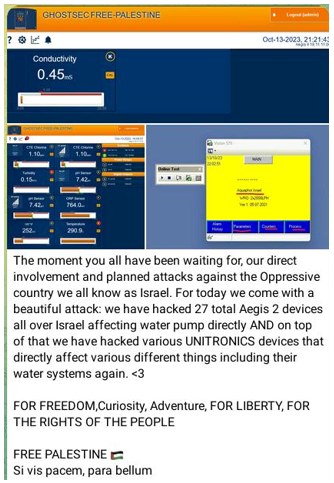
Figure 3. GhostSec claiming assault on Unitronics units in Israel. (Source: Secure Works)
Cyber Av3ngers are energetic on social media and frequently declare assaults towards Israel’s essential nationwide infrastructure. One of the Telegram posts hyperlinks to his July 2020 article describing an assault that allegedly concerned 150 Israeli rail system servers and affected 28 practice stations. The Cyber Avengers (because it was spelled on the time with out the “3”) claimed duty for the assault. The time of the assault coincided with the airstrike that killed Islamic Republican Guard Corps (IRGC) commander Qassem Soleimani on January 3. In September 2023, hacktivists used the X account to advertise information believed to have been stolen throughout the July assault. They provided to promote details about 3,000 staff and his over 10 million journeys, together with passenger particulars, for 4 BTC (roughly 108,000 USD on the time of posting).
Throughout October 2023, cyberattackers continued to put up claims of high-profile assaults towards energy vegetation, gasoline stations, and different essential nationwide infrastructure property. However, most of those claims have been uncovered as exaggerations or fabrications. The group claimed that Israel’s Dorado energy plant had been attacked and posted photographs of the SCADA system on Telegram as proof (see Figure 5). However, safety researchers decided that these “leaked” paperwork have been recycled and reused from assaults by the Moses Staff hacktivist group, and CTU’s evaluation linked them to the IRGC. Suggests. CTU researchers affiliate the Moses Staff persona together with his COBALT SAPLING menace group. The Cyber Av3ngers might have reused photographs downloaded from the Moses Staff leak website, or the 2 teams could also be working collectively behind the scenes.
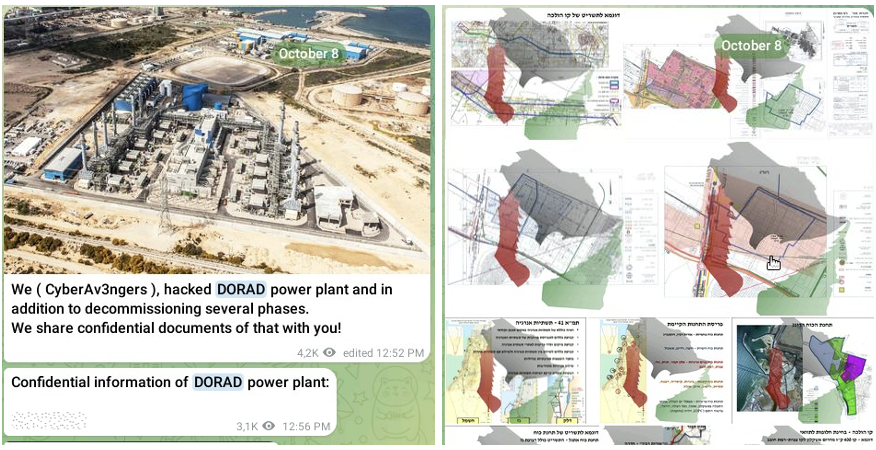
Figure 5. Cyber attacker claiming assault on Dorad energy plant. (Source: Secure Works)
Just as COBALT SAPLING operates the Moses Staff and Abraham’s Ax personas, Cyber Av3ngers are doubtless being operated by Iranian state-sponsored menace teams. This evaluation relies on Iranian information media references to earlier assaults, which have been poorly reported by different media shops, and on CISA’s discovering that the November 2023 assault was carried out by Revolutionary Guards-affiliated forces. ing. Cybercriminals can also use digital reconnaissance methods, akin to looking web analysis providers (Shodan, Censys, and many others.) to determine weak Unitronics units, just like ways utilized by Iranian teams. The July 2021 report discusses leaked paperwork mentioned to have been compiled by a staff throughout the Shahid Qabeh unit referred to as “Intelligence Team 13.” The doc particulars digital reconnaissance of commercial programs akin to ships’ ballast water pumps, gas pump programs and maritime communication programs beginning within the second half of 2020.
CTU researchers advocate that organizations utilizing Unitronics units evaluate the data within the CISA suggestions and apply the steering as acceptable. The UK’s National Cyber Security Center (NCSC) echoed CISA’s recommendation.
For extra data on scan-and-exploit assaults and different threats, take a look at our 2023 State of Threats report. If you want speedy help with an incident, please contact the Secureworks Incident Response staff.

