VMware has confirmed {that a} important vCenter Server distant code execution vulnerability patched in October is now beneath energetic exploitation.
vCenter Server is a administration platform for VMware vSphere environments that helps directors handle ESX and ESXi servers and digital machines (VMs).
“VMware has confirmed that exploitation of CVE-2023-34048 has occurred within the wild,” the corporate mentioned in an replace added to the unique advisory this week.
The vulnerability was reported by Trend Micro vulnerability researcher Grigory Dorodnov and is brought on by an out-of-bounds write weak spot in vCenter’s DCE/RPC protocol implementation.
Attackers can exploit it remotely in low-complexity assaults with excessive confidentiality, integrity, and availability influence that don’t require authentication or consumer interplay. Due to its important nature, VMware has additionally issued safety patches for a number of end-of-life merchandise with out energetic assist.
Network entry brokers wish to take over VMware servers after which promote on cybercrime boards to ransomware gangs for straightforward entry to company networks. Many ransomware teams (like Royal, Black Basta, LockBit, and, extra lately, RTM Locker, Qilin, ESXiArgs, Monti, and Akira) are actually recognized for immediately concentrating on the victims’ VMware ESXi servers to steal and encrypt their recordsdata and demand big ransoms.
According to Shodan knowledge, greater than 2,000 VMware Center servers are presently uncovered on-line, doubtlessly susceptible to assaults and exposing company networks to breach dangers given their vSphere administration position.
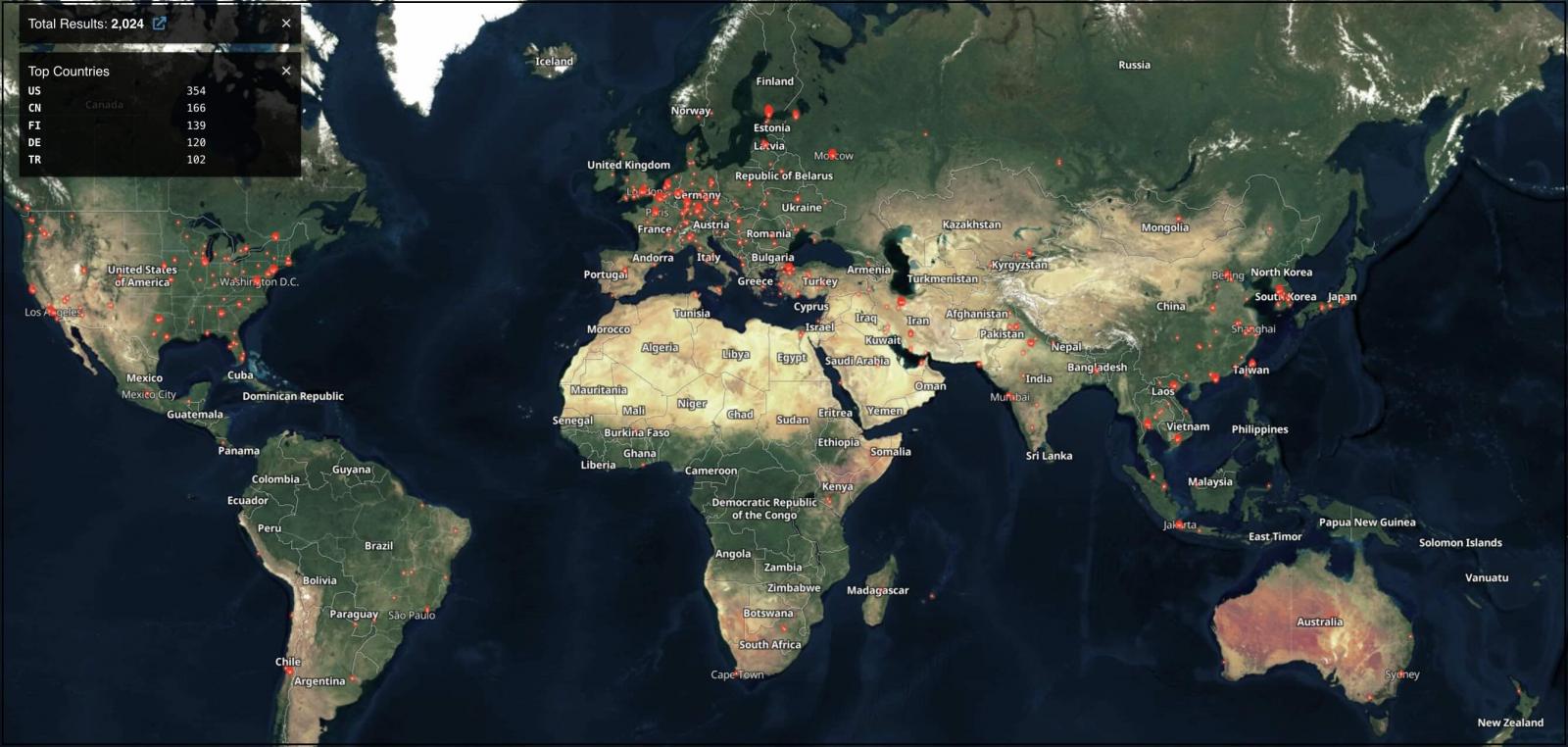
Because there isn’t any workaround, VMware has urged admins who cannot patch their servers to strictly management community perimeter entry to vSphere administration parts.
“VMware strongly recommends strict community perimeter entry management to all administration parts and interfaces in vSphere and associated parts, resembling storage and community parts, as a part of an total efficient safety posture,” the corporate warned.
The particular community ports linked to potential exploitation in assaults concentrating on this vulnerability are 2012/tcp, 2014/tcp, and 2020/tcp.
In June, VMware additionally mounted a number of high-severity vCenter Server safety flaws posing code execution and authentication bypass dangers to susceptible servers.
The identical week, the corporate mounted an ESXi zero-day utilized by Chinese state hackers in knowledge theft assaults and warned clients of one other actively exploited important Aria Operations for Networks flaw.
Since the start of the 12 months, IT admins and safety groups have needed to deal with warnings of a number of safety vulnerabilities beneath energetic exploitation, together with zero-days affecting Ivanti Connect Secure, Ivanti EPMM, and Citrix Netscaler servers.

