Energy administration and automation large Schneider Electric suffered a Cactus ransomware assault resulting in the theft of company information, in response to folks aware of the matter.
BleepingComputer has discovered that the ransomware assault hit the corporate’s Sustainability Business division earlier this month on January seventeenth.
The assault disrupted a few of Schneider Electric’s Resource Advisor cloud platform, which continues to undergo outages at this time.
The ransomware gang reportedly stole terabytes of company information through the cyberattack and is now extorting the corporate by threatening to leak the stolen information if a ransom demand isn’t paid.
While it’s not recognized what kind of knowledge was stolen, the Sustainability Business division gives consulting providers to enterprise organizations, advising on renewable vitality options and serving to them navigate complicated local weather regulatory necessities for firms worldwide.
Source: BleepingComputer
Customers of Schneider Electric’s Sustainability Business division embrace Allegiant Travel Company, Clorox, DHL, DuPont, Hilton, Lexmark, PepsiCo, and Walmart.
The stolen information may include delicate details about clients’ energy utilization, industrial management and automation techniques, and compliance with environmental and vitality rules.
It isn’t recognized if Schneider Electric will probably be paying a ransom demand, but when one isn’t paid, we’ll probably see the ransomware gang leaking the stolen information as they’ve performed after earlier assaults.
In an announcement to BleepingComputer, Schneider Electric confirmed that its Sustainability Business division suffered a cyberattack and that information was accessed by the risk actors. However, the corporate says the assault was restricted to this one division and didn’t have an effect on different elements of the corporate.
“From a restoration standpoint, Sustainability Business is performing remediation steps to make sure that enterprise platforms will probably be restored to a safe atmosphere. Teams are at present testing the operational capabilities of impacted techniques with the expectation that entry will resume within the subsequent two enterprise days.
From a containment standpoint, as Sustainability Business is an autonomous entity working its remoted community infrastructure, no different entity inside the Schneider Electric group has been affected.
From an influence evaluation standpoint, the continuing investigation reveals that information has been accessed. As extra info turns into out there, the Sustainability Business division of Schneider Electric will proceed the dialogue instantly with its affected clients and can proceed to offer info and help as related.
Schneider Electric is a French multinational firm that manufactures vitality and automation merchandise starting from family electrical elements present in massive field shops to enterprise-level industrial management and constructing automation merchandise.
Schneider Electric had $28.5 billion in income for the primary 9 months of 2023 and employs over 150,000 folks worldwide. Schneider Electric is anticipated to launch its 2023 full-year monetary outcomes subsequent month.
Some of its well-known shopper manufacturers embrace Homeline, Square D, and APC, the producer of extensively used uninterruptible energy provide (UPS) gadgets.
Schneider Electric was beforehand focused within the widespread MOVEit information theft assaults by the Clop ransomware gang that impacted over 2,700 firms.
If you’ve got any info relating to this incident or another undisclosed assaults, you may contact us confidentially through Signal at 646-961-3731 or at ideas@bleepingcomputer.com.
Who is Cactus ransomware
The Cactus ransomware operation launched in March 2023 and has since amassed quite a few firms that they declare had been breached in cyberattacks.
Like all ransomware operations, the risk actors will breach company networks via bought credentials, partnerships with malware distributors, phishing assaults, or by exploiting vulnerabilities.
Once the risk actors achieve entry to a community, they quietly unfold to different techniques whereas stealing company information on servers.
After stealing the information and gaining administrative privileges on the community, the risk actors encrypt information and go away ransom notes behind.
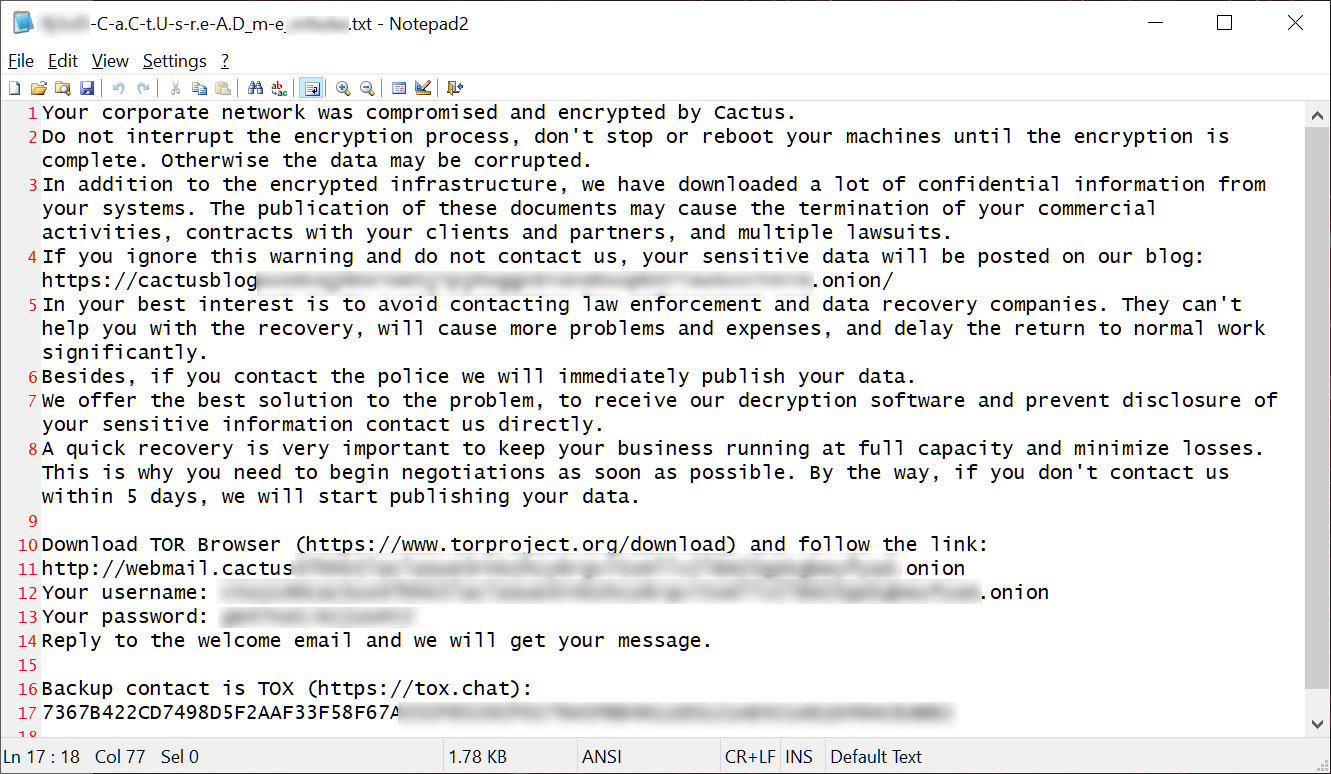
Source: BleepingComputer
The risk actors will then conduct double-extortion assaults, which is once they demand a ransom to obtain each a file decryptor and promise to destroy and never leak stolen information.
For these firms who don’t pay a ransom, the risk actors will leak their stolen information on a knowledge leak website.
At this time, there are over 80 firms listed on Cactus’ information leak website whose information has been leaked or the risk actors warn they’ll achieve this.

