Today, Ivanti warned of two extra vulnerabilities impacting Connect Secure, Policy Secure, and ZTA gateways, one among them a zero-day bug already below energetic exploitation.
The zero-day flaw (CVE-2024-21893) is a server-side request forgery vulnerability within the gateways’ SAML part that allows attackers to bypass authentication and entry restricted sources on weak units.
A second flaw (CVE-2024-21888) within the gateways’ internet part permits risk actors to escalate privileges to these of an administrator.
“As a part of our ongoing investigation into the vulnerabilities reported on 10 January in Ivanti Connect Secure, Ivanti Policy Secure and ZTA gateways, we now have found new vulnerabilities. These vulnerabilities impression all supported variations – Version 9.x and 22.x,” the corporate stated right this moment.
“We don’t have any proof of any clients being impacted by CVE-2024-21888 presently. We are solely conscious of a small variety of clients who’ve been impacted by CVE-2024-21893 presently.”
“It is essential that you simply instantly take motion to make sure you are totally protected,” Ivanti warned.
This was disclosed in a non-public safety advisory (now publicly out there) detailing the 2 flaws on January 22, greater than per week earlier than the corporate publicly disclosed the 2 bugs.
Ivanti has launched safety patches to deal with each flaws for some affected ZTA and Connect Secure variations, and it gives mitigation directions for units nonetheless ready for a patch.
Patches for 2 extra actively exploited zero-days
The firm additionally launched patches right this moment for 2 different zero-days disclosed in early January—an authentication bypass (CVE-2023-46805) and a command injection (CVE-2024-21887)—chained in widespread assaults to deploy malware on weak ICS, IPS, and ZTA gateways since January 11.
Ivanti additionally launched mitigation measures to dam assault makes an attempt and restoration directions designed to assist restore compromised units and produce them again on-line.
Threat monitoring platform Shadowserver presently tracks over 24,700 Internet-exposed ICS VPN gateways, over 7,200 within the United States (Shodan additionally sees over 22,000 Ivanti ICS VPNs uncovered on-line).
Shadowserver additionally retains observe of compromised Ivanti VPN cases worldwide every day, with over 460 compromised units found on January 30 alone.
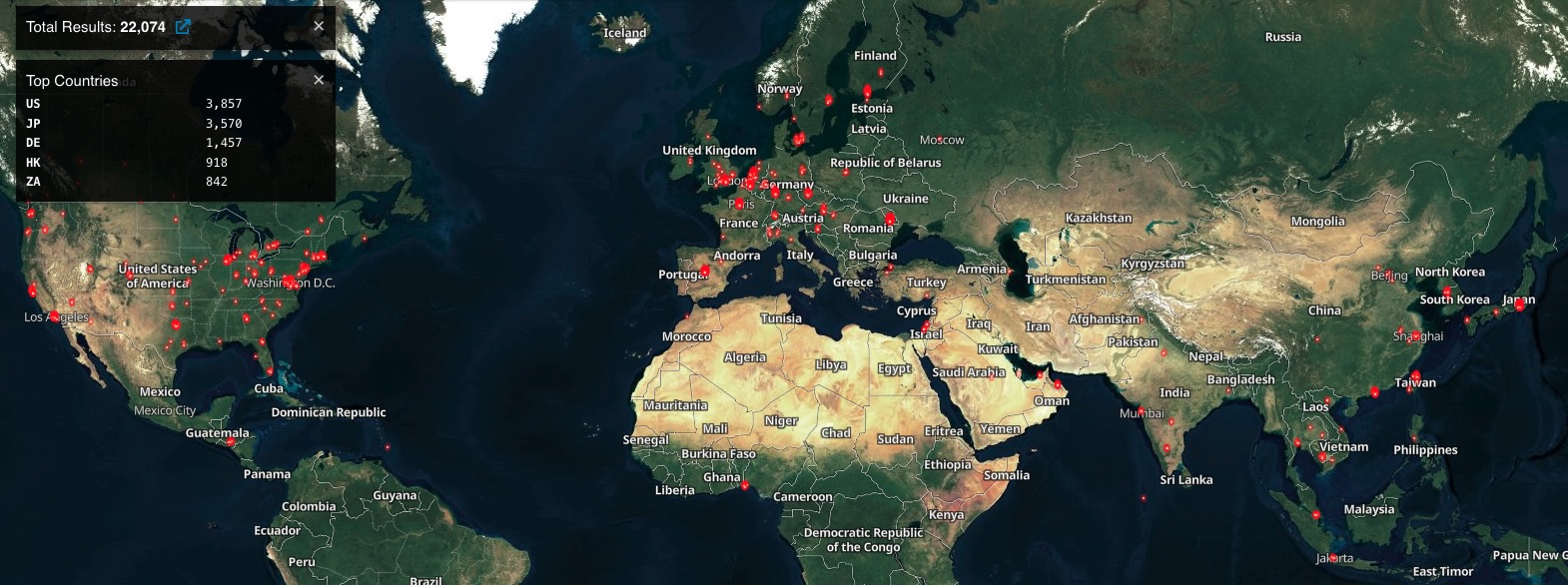
CISA additionally issued 2024’s first emergency directive (ED 24-01), ordering federal businesses to right away mitigate the CVE-2023-46805 and CVE-2024-21887 Ivanti zero-day flaws in response to mass exploitation by a number of risk actors.
When chained, the 2 zero-days let attackers transfer laterally inside victims’ networks, steal knowledge, and set up persistent entry by deploying backdoors.
The listing of victims found to date contains authorities and army organizations worldwide, nationwide telecom firms, and protection contractors, in addition to banking, finance, and accounting organizations and aerospace, aviation, and tech corporations.
They all range considerably in dimension, starting from small companies to a few of the largest multinational conglomerates, together with a number of Fortune 500 firms from varied trade sectors.
Mandiant discovered 5 customized malware strains deployed in these intensive assaults that assist risk actors steal credentials, deploy webshells, and drop extra malicious payloads.
Volexity and GreyNoise have additionally noticed attackers deploying XMRig cryptocurrency miners and Rust-based malware payloads on some victims’ compromised programs.

