CISA has ordered US federal companies to disconnect all Ivanti Connect Secure and Policy Secure VPN home equipment susceptible to a number of actively exploited bugs earlier than Saturday.
This required motion is a part of a supplemental course to this 12 months’s first emergency directive (ED 24-01) issued final week that mandates Federal Civilian Executive Branch (FCEB) companies to urgently safe all ICS and IPS units on their community in opposition to two zero-days flaws in response to in depth exploitation within the wild by a number of menace actors.
Ivanti home equipment are presently focused in assaults chaining the CVE-2023-46805 authentication bypass and the CVE-2024-21887 command injection safety flaws since December as zero-days.
The firm additionally warned of a 3rd actively exploited zero-day (a server-side request forgery vulnerability tracked as CVE-2024-21893), permitting menace actors to bypass authentication on susceptible ICS, IPS, and ZTA gateways.
On Wednesday, Ivanti launched safety patches for some software program variations affected by the three flaws, and it additionally gives mitigation directions for units nonetheless ready for a patch or that can not be secured instantly in opposition to ongoing assaults.
Yesterday, Ivanti urged clients to manufacturing facility reset susceptible home equipment earlier than patching to thwart attackers’ makes an attempt to achieve persistence on their community between software program upgrades.
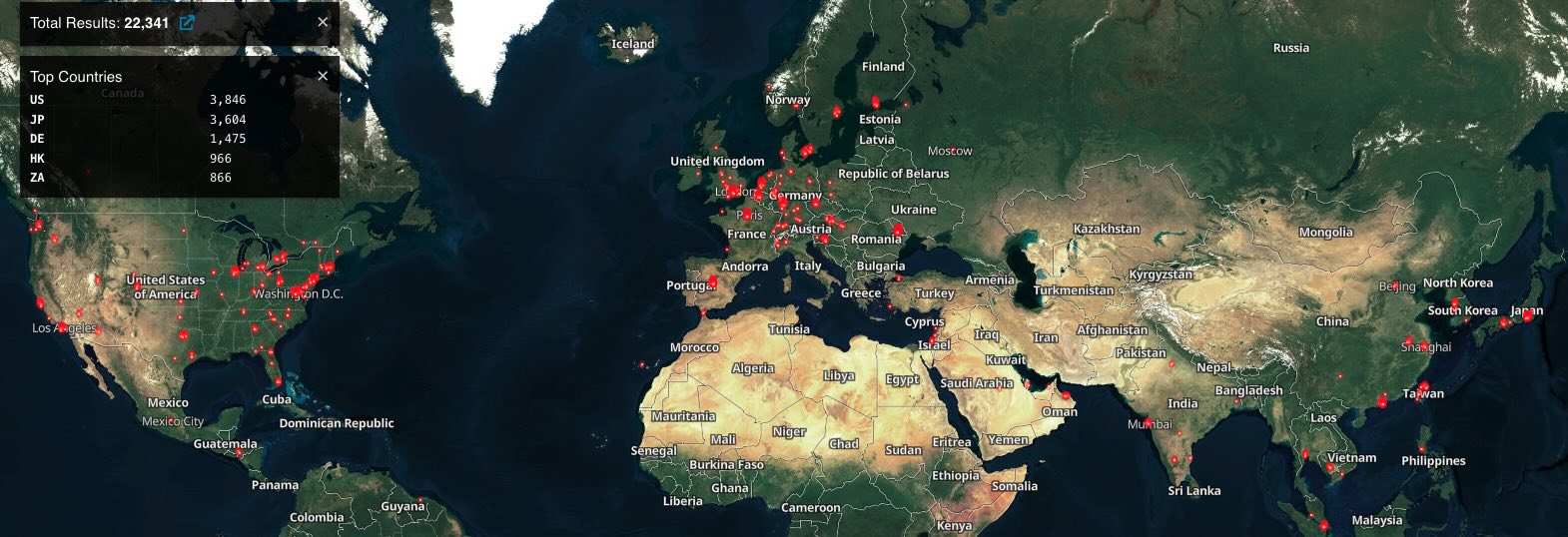
Shodan presently sees over 22,000 Ivanti ICS VPNs uncovered on-line, whereas menace monitoring platform Shadowserver tracks greater than 21,400.
Shadowserver additionally screens the variety of Ivanti VPN cases compromised worldwide every day, with virtually 390 hacked units found on January 31.
CISA: Disconnect all Ivanti VPNs by Saturday
In response to the “substantial menace” and important threat of safety breaches posed by compromised Ivanti VPN home equipment, CISA now mandates all federal companies to “disconnect all cases of Ivanti Connect Secure and Ivanti Policy Secure resolution merchandise from company networks,” “as quickly as potential” however no later than 11:59 PM on Friday, February 2.
After the units are faraway from the community, the companies should additionally maintain attempting to find indicators of compromise on methods linked to, or not too long ago related to, the disconnected Ivanti units.
Furthermore, they have to proceed monitoring authentication or identification administration providers inclined to publicity, isolating enterprise methods, and auditing privilege-level entry accounts.
To carry the Ivanti home equipment again on-line, the companies should export their configuration, manufacturing facility reset them, rebuild them utilizing patched software program variations, reimport the backed-up configs, and revoke all related or uncovered certificates, keys, and passwords.
In the subsequent stage, federal companies that had impacted Ivanti merchandise on their networks also needs to assume that every one linked area accounts have been compromised and disable joined/registered units (in cloud environments) or carry out a double password reset for all accounts and revoke Kerberos tickers and cloud tokens (in hybrid setups).
After every restoration stage, companies should report their standing throughout all required actions to CISA utilizing a CyberScope template offered by the cybersecurity company. They’ll even have to offer updates on their progress upon CISA’s request or when all actions are full.
“This Supplemental Direction stays in impact till CISA determines that every one companies working affected software program have carried out all required actions from this Direction or the Direction is terminated by different applicable motion,” CISA stated.

