
The Iranian menace actor often known as MuddyWater is believed to be attributable to a brand new command and management (C2) infrastructure referred to as DarkBeatC2, making it the newest instrument after SimpleHarm, MuddyC3, PhonyC2, and MuddyC2Go.
“While we might have switched to new distant administration instruments or modified our C2 framework, MuddyWater’s methodology stays the identical,” Simon Kenin, a safety researcher at Deep Instinct, wrote in a technical report printed final week. It is said in
MuddyWater, also referred to as Boggy Serpens, Mango Sandstorm, and TA450, is assessed to be affiliated with Iran’s Ministry of Intelligence and Security (MOIS). This marketing campaign is understood to be energetic since not less than 2017 and entails orchestrating spear phishing assaults and deploying varied official distant monitoring and administration (RMM) options to compromised techniques.
Microsoft’s earlier findings hyperlink this group to a different Iranian menace exercise cluster tracked as Storm-1084 (also referred to as DarkBit), the latter for organizing devastating wiper assaults in opposition to Israeli organizations. It has been proven that entry is on the market.

The newest assault marketing campaign, the main points of which have been beforehand disclosed by Proofpoint final month, concerned compromised accounts containing hyperlinks and attachments hosted on providers akin to Egnyte to ship Atera Agent software program. It begins with a spear phishing e mail despatched from .
One of the URLs in query is “kinneretacil.egnyte.”[.]com,” and the subdomain “kinneretacil” refers to “kinneret.ac.il,” an Israeli instructional establishment and Rashim buyer. This group was in flip compromised by Lord Nemesis (also referred to as Nemesis Kitten or TunnelVision) as a part of: Supply chain assault concentrating on tutorial departments in Japan.
Lord Nemesis is suspected of a “pretend” operation in opposition to Israel. It can also be price noting that Nemesis Kitten is a personal contractor referred to as Najee Technology, a subgroup inside Mint Sandstorm that’s supported by the Iranian Islamic Revolutionary Guards Corps (IRGC). The firm was sanctioned by the US Treasury Department in September 2022.
“This is necessary as a result of if ‘Lord Nemesis’ was in a position to infiltrate Rasim’s e mail system, they might use the administrator account that we now know to have been obtained from ‘Rasim’ to entry Rasim’s clients. ‘s e mail system,” Kenin defined.
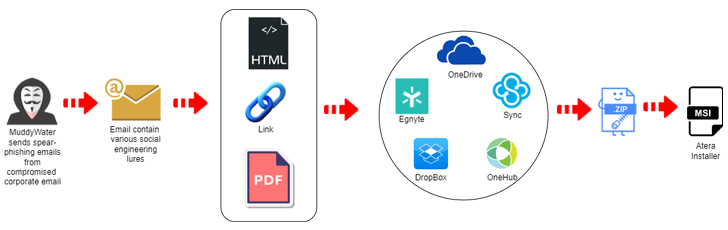
The community connections elevate the chance that MuddyWater used an e mail account related to Kinneret to distribute the hyperlink, giving the message an phantasm of belief and tricking recipients into clicking.
“While not conclusive, the timeframe and circumstances of occasions point out the potential of a handover or collaboration between the IRGC and MOIS to inflict as a lot injury as attainable on Israeli entities and people. “There are,” Kenin added.
The assault can also be notable for counting on a set of domains and IP addresses, collectively often known as DarkBeatC2, which can be accountable for managing contaminated endpoints. This is achieved by way of PowerShell code designed to determine a reference to the C2 server upon preliminary entry gained by way of different means.
According to unbiased analysis from Palo Alto Networks Unit 42, the attacker was noticed abusing the AutodialDLL characteristic within the Windows registry to sideload a malicious DLL and in the end arrange a reference to the DarkBeatC2 area. I’m.
This mechanism contains, amongst different issues, establishing persistence by way of a scheduled job that runs PowerShell and makes use of the AutodialDLL registry key to load DLLs for the C2 framework. A cybersecurity firm introduced that the expertise was utilized in a cyberattack concentrating on nameless targets within the Middle East.
Other strategies utilized by MuddyWater to determine a C2 connection embody the usage of a first-stage payload delivered through spear-phishing emails and the usage of DLL sideloading to execute malicious libraries. included.

“This framework is much like the earlier C2 framework used at MuddyWater,” Kenin stated. “PowerShell continues to be their ‘bread and butter.’ ”
Curious Serpens targets protection sector with FalseFont backdoor
The disclosure comes after Unit 42 found a backdoor referred to as FalseFont utilized by the Iranian menace actor often known as Peach Sandstorm (also referred to as APT33, Curious Serpens, Elfin, and Refined Kitten) in assaults concentrating on the aerospace and protection sector. This was performed when the construction was unzipped.
“Threat actors are mimicking official human assets software program and utilizing pretend recruitment processes to trick victims into putting in backdoors,” stated safety researchers Tom Fakterman, Daniel Frank, and Jerome Tujague. stated that FalseFont is “very focused.”
Once put in, a login interface impersonating an aerospace firm is displayed, and the credentials entered by the sufferer together with instructional and employment historical past are captured in JSON format on a C2 server managed by the menace actor.
In addition to a graphical consumer interface (GUI) part for consumer enter, this implant establishes persistence on the system, collects system metadata, and executes instructions and processes despatched from the C2 server. Start the part secretly within the background.
Other options of FalseFont embody the power to obtain and add information, steal credentials, seize screenshots, terminate sure processes, run PowerShell instructions, and self-update malware.
Did you discover this text attention-grabbing? Follow us Twitter ○ You can learn extra unique content material from us on LinkedIn.
Source hyperlink

